A Security Analysis of Whatsapp Ios Mobile Application
This research presents an investigation into WhatsApp’s on-device data storage on iOS. WhatsApp is one of the most widely used messaging application and hence it is required that a secured on-device storage mechanism be implemented to complement Apple’s security measures for their devices. This will help protect a user’s data in instances where his/her device is compromised physically. The research presents a security analysis on the storage format of data used by WhatsApp on end-users' devices.
Introduction
The team behind Uc0ver [1] released an iOS 11.0 - 13.5.5 jailbreak for all iPhones and iPads. This is the first iOS jailbreak in years to use a 0-day exploit as previous tools relied on a 1-day exploit or other security lapses from Apple’s part [2].
“Jailbreaking” is a privilege escalation of an Apple device for the purpose of removing software restrictions imposed by Apple on iOS. It permits root access in Apple’s mobile operating system, allowing the installation of software that is unavailable through the official Apple App Store. Apple states that Jailbreaking an Apple device eliminates security layers designed to protect one’s personal information [3].
This research explores how data is stored securely by WhatsApp Messenger (a cross-platform messaging and Voice-over-IP service) on an iPhone.
Research Approach
WhatsApp Messenger, or simply WhatsApp allows users to send text messages and voice messages, make voice and video calls, and share images, documents, user locations and other media. In January 2018, WhatsApp released a standalone business app targeted at small business owners, called WhatsApp Business, to allow companies to communicate with customers who use the standard WhatsApp client. This research does not explore on-device data security of the WhatsApp Business application.
The standard security mechanism put in place by Apple prevents unauthorized access to an application’s data folder; which is circumvented through jailbreak. This research uses an iPhone 7 for the security analysis. The security analysis focuses on only WhatsApp’s on-device application data storage.
Security Analysis
The WhatsApp version used in this research was 2.20.52.7. A brief content of the application’s info.plist is shown in Fig. 1.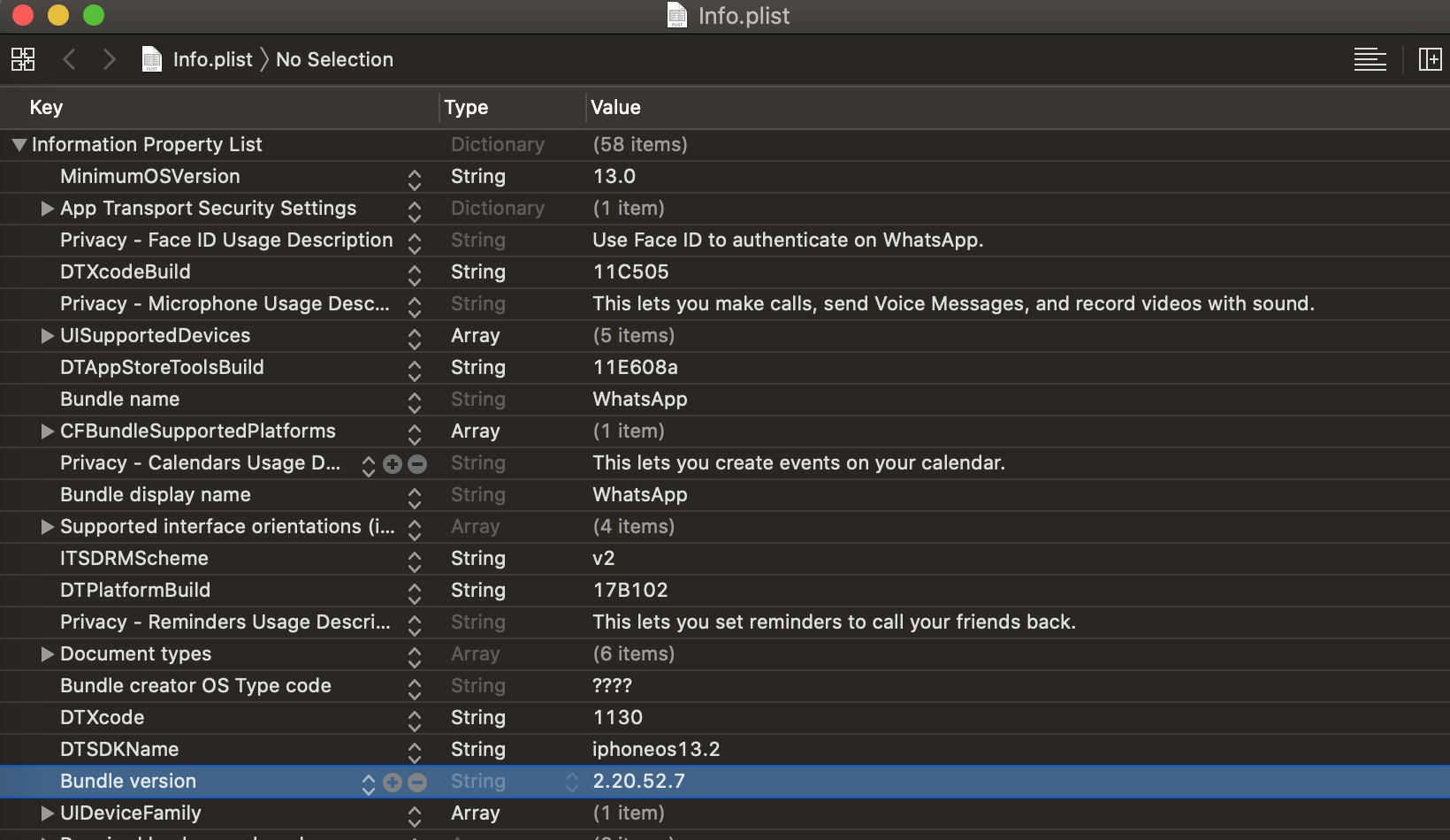
Fig. 1: Info.plist Contents
The content’s of WhatsApp’s application folder is shown in Fig. 2.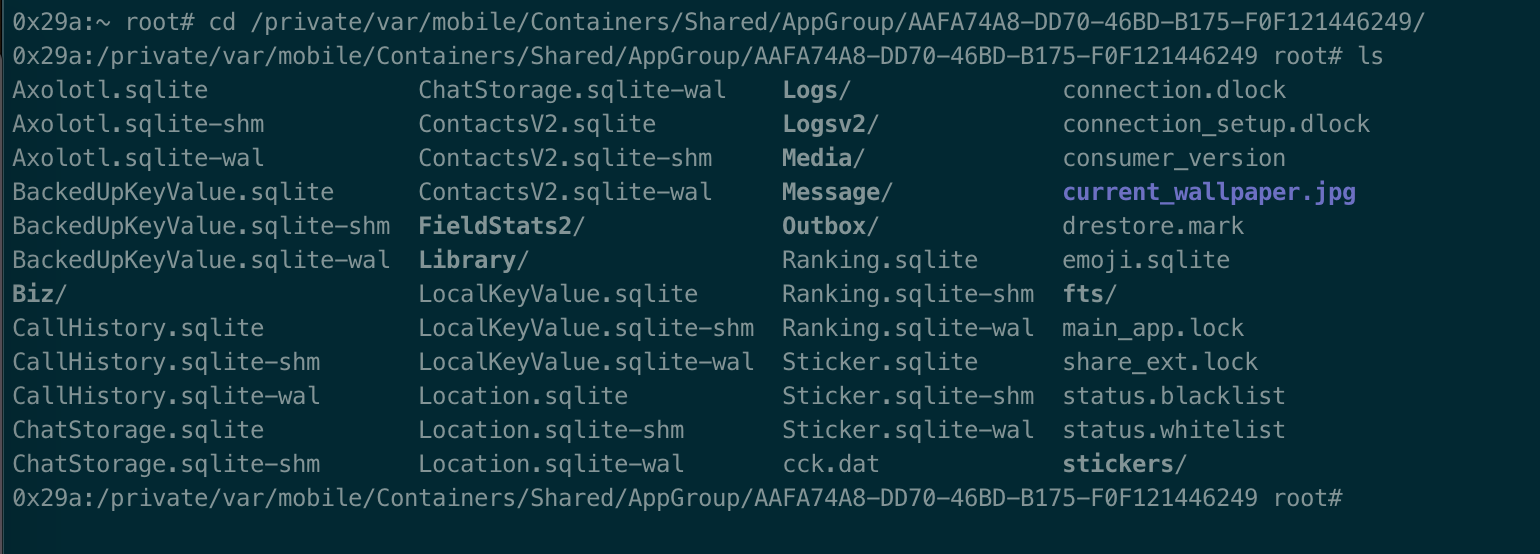
Fig. 2: Contents of Application Data
The Biz folder contains an SQLite file; which stores the details of all WhatsApp Business clients that a user has in his/her contacts. Details of such clients are stored in plain text in the SQLite file as shown in Figs. 3, 4 and 5. This details include their business names, phone numbers, business addresses, business location cooordinates, email addresses etc.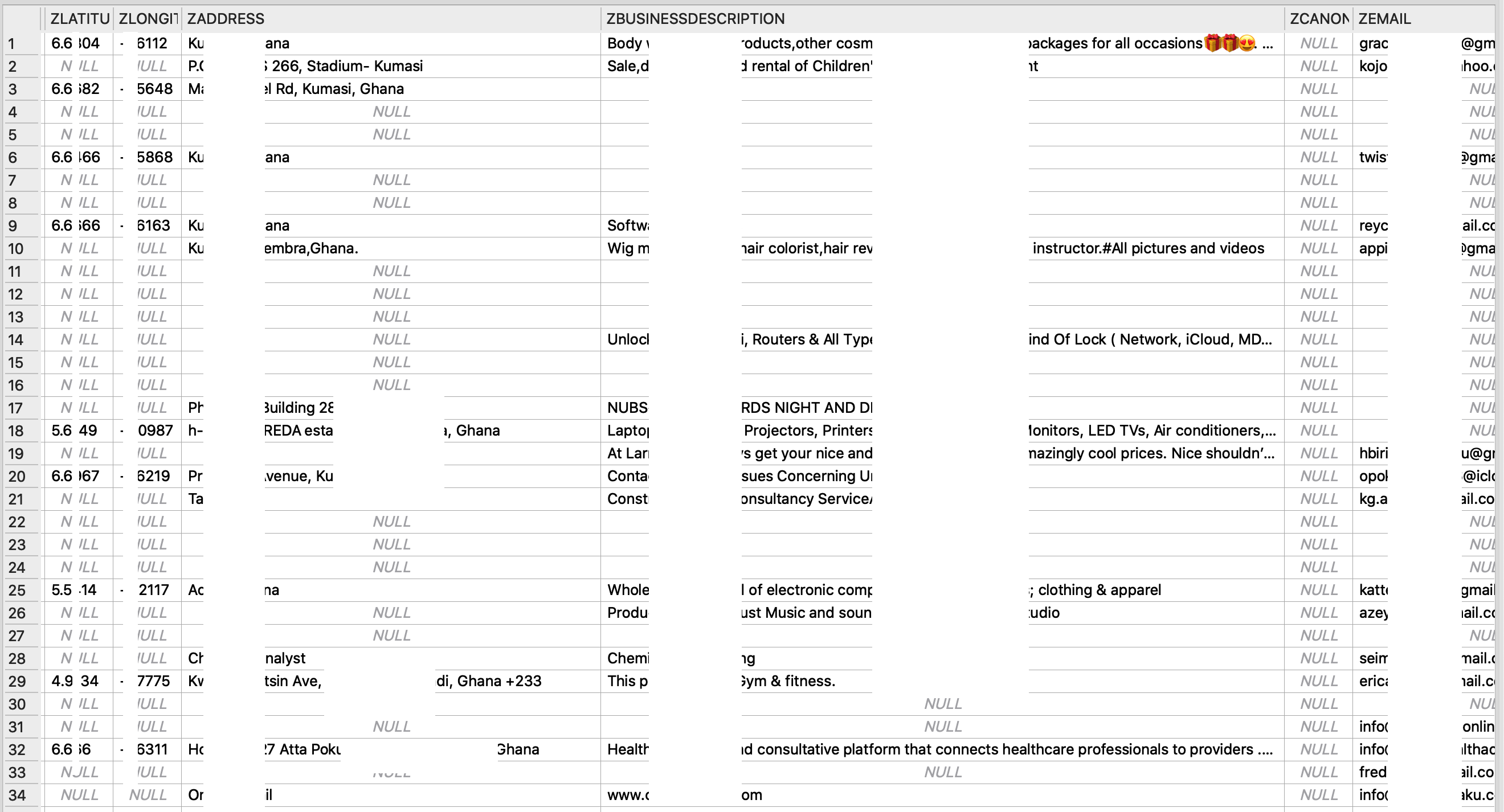
Fig. 3: Details of WhatsApp Business Clients
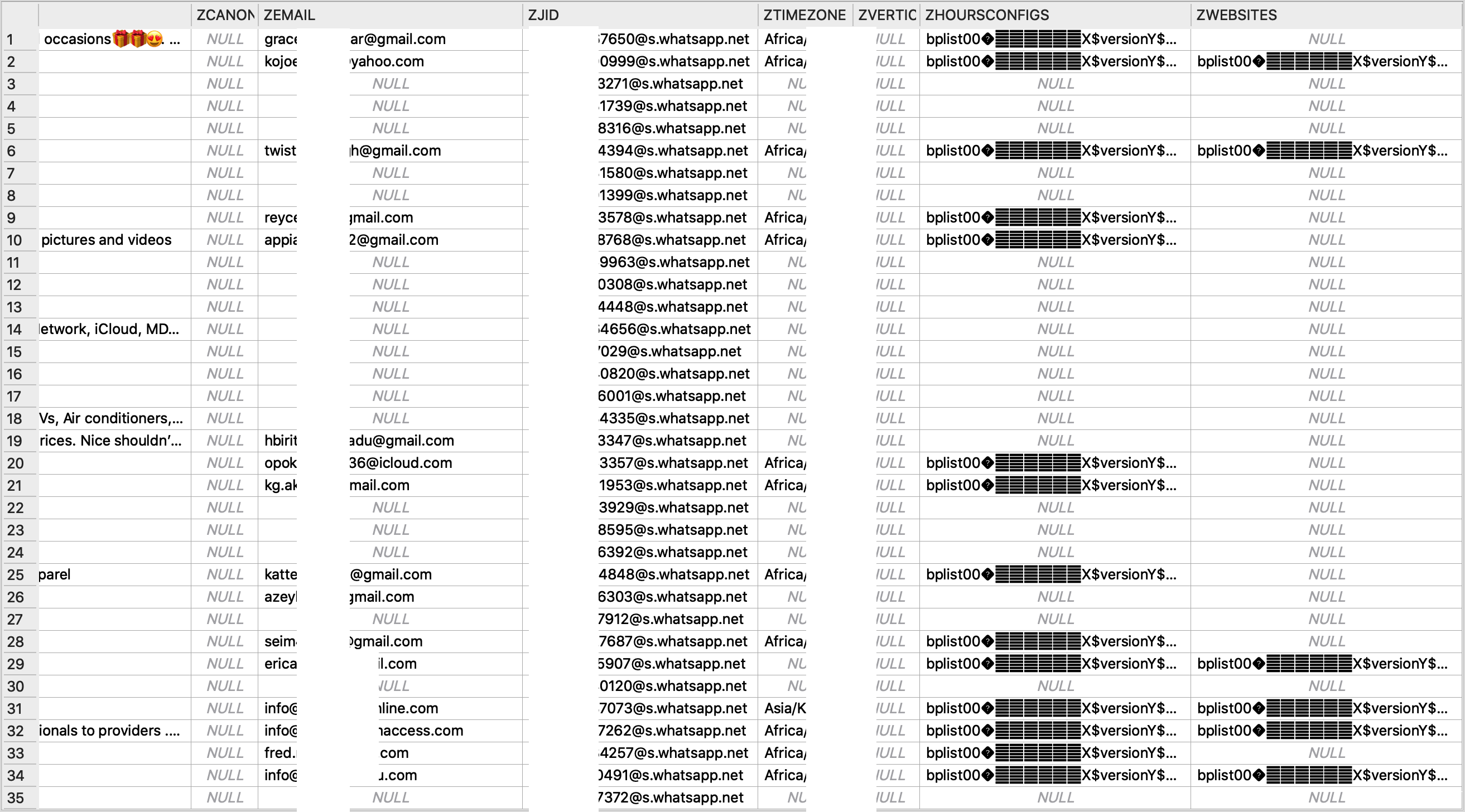
Fig. 4: Details of WhatsApp Business Clients
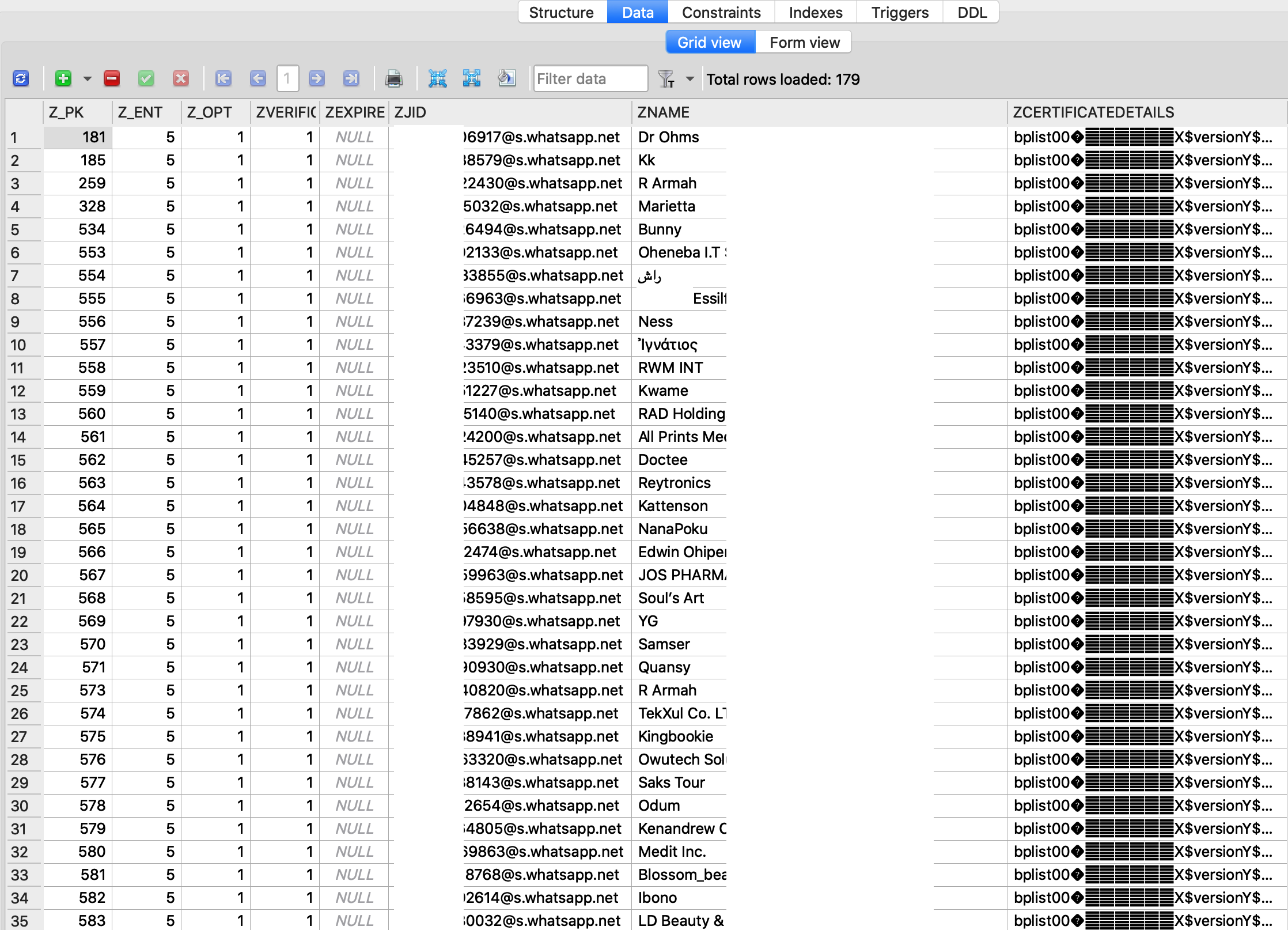
Fig. 5: Details of WhatsApp Business Clients
It was realized that WhatsApp filters certain keywords from all messages sent/received. This is stored in an SQLite file called “ChatSearchV5f”. A sample content is shown in Fig. 6. As at the time of writing, it is unknown what such information is used for.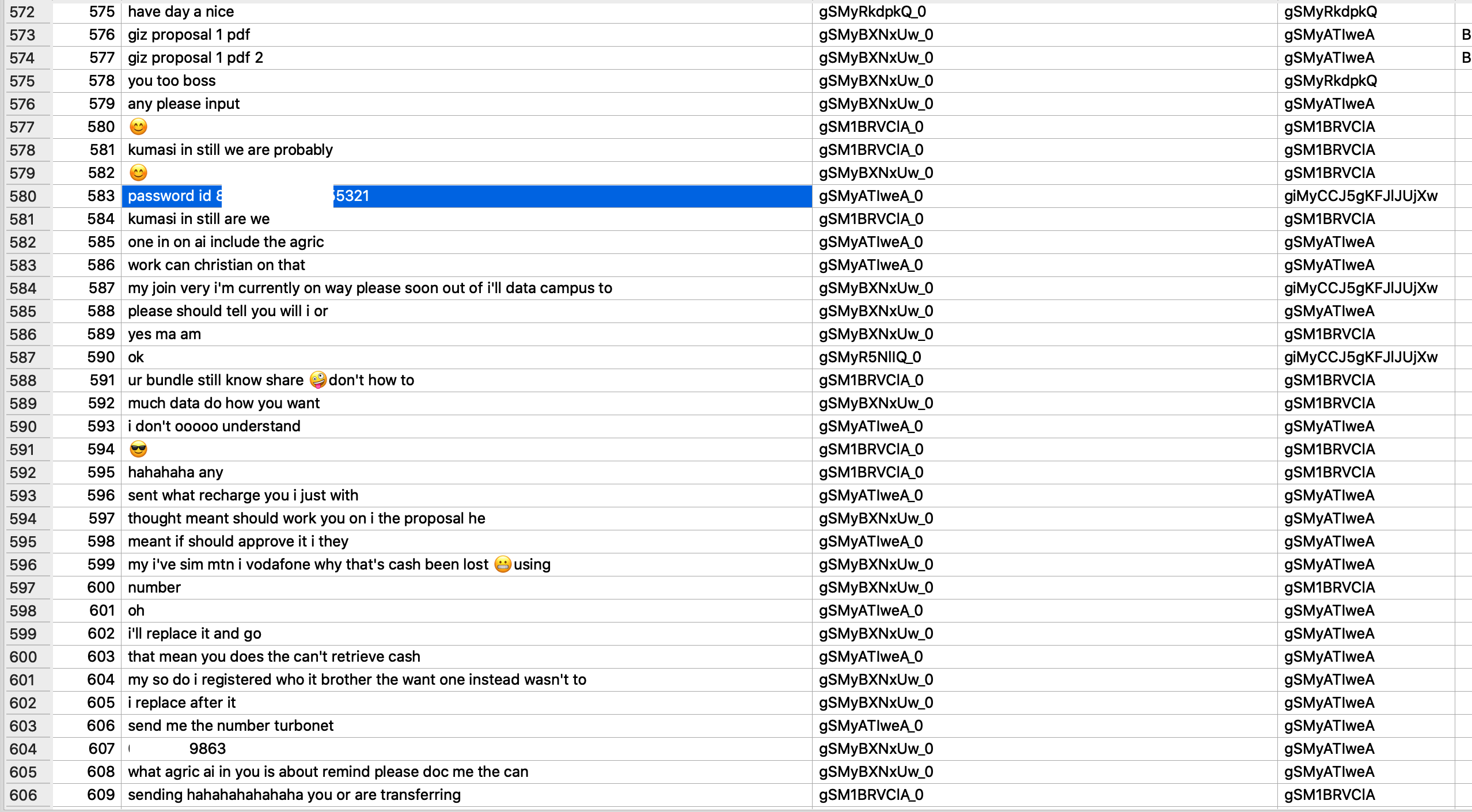
Fig. 6: Chat Search
‘Status’ images and videos are stored in the media library folder. The images have a .thumb extension whereas the videos have no file extension. It was realized that the streaming files are mp4 encoded (shown in Fig. 7). Adding .mp4 as an extension to the streaming files enables you to play them.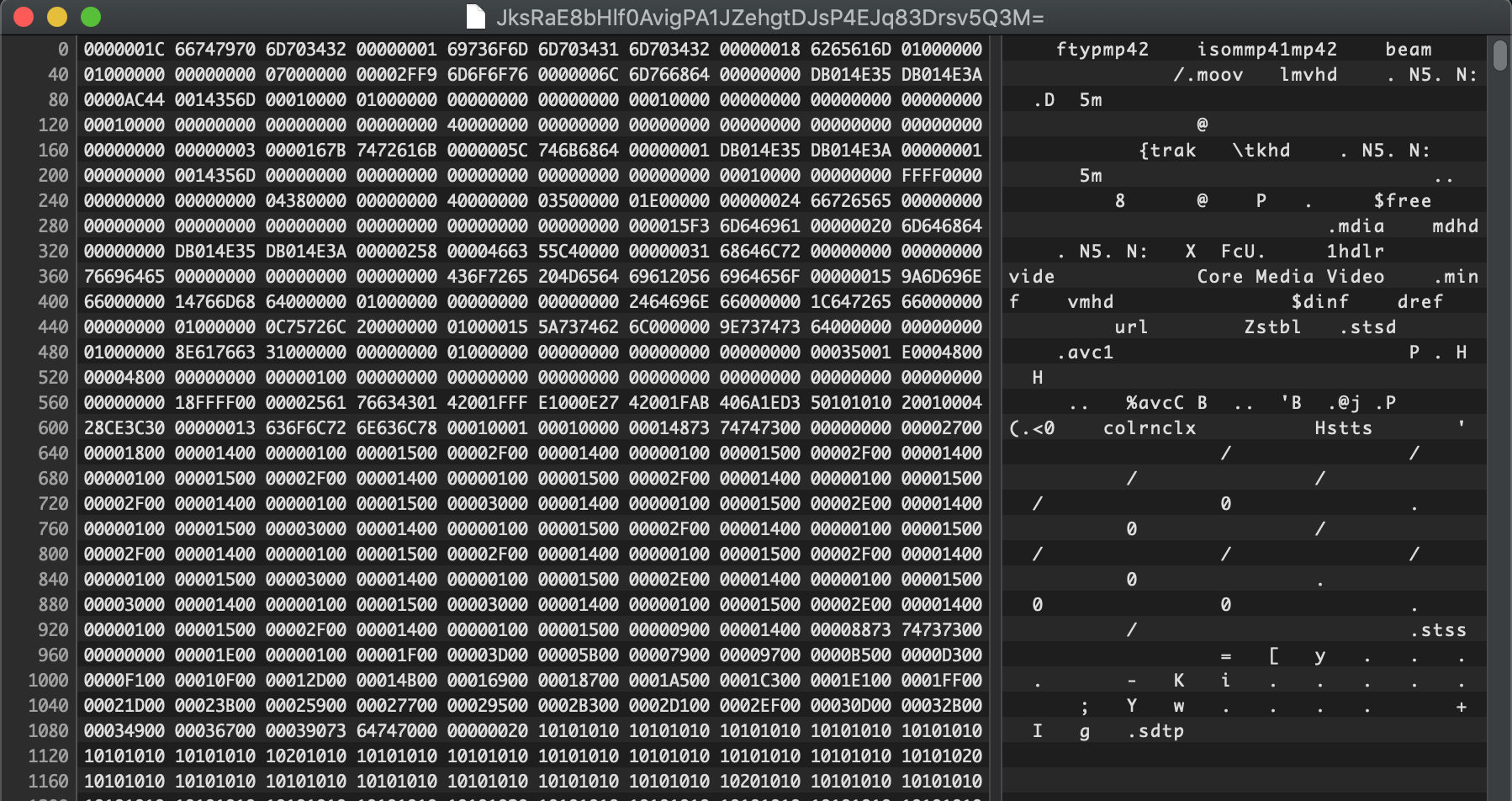
Fig. 7: Video Extension
Chat messages are stored in “CallHistory.sqlite”. This SQLite file stores names of groups a user belongs to (shown in Fig. 8), messages sent to and received in the group, messages sent/received from other users (shown in Fig. 9) and links to encrypted images and videos sent/received (shown in Fig. 10 and 11).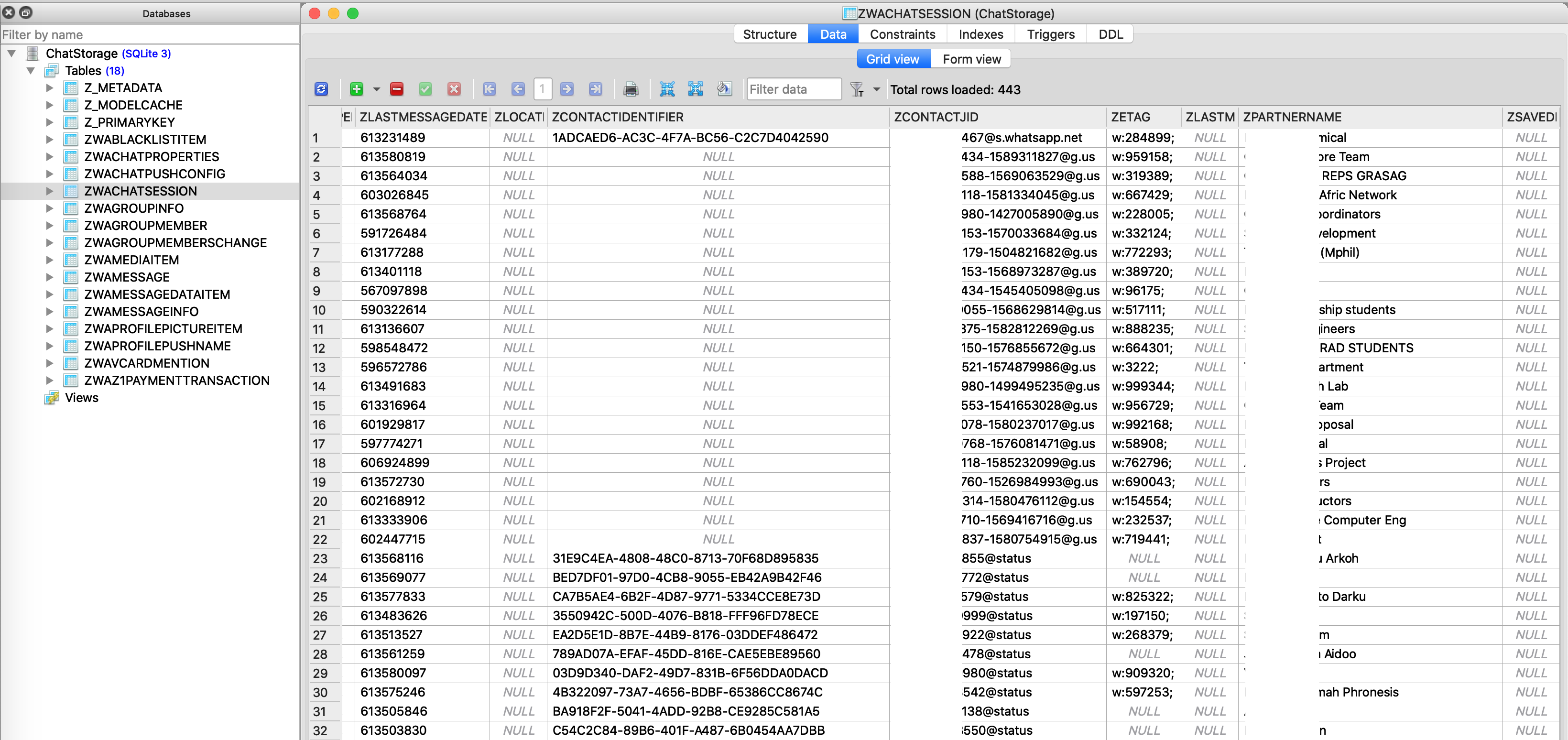
Fig. 8: User’s WhatsApp Groups
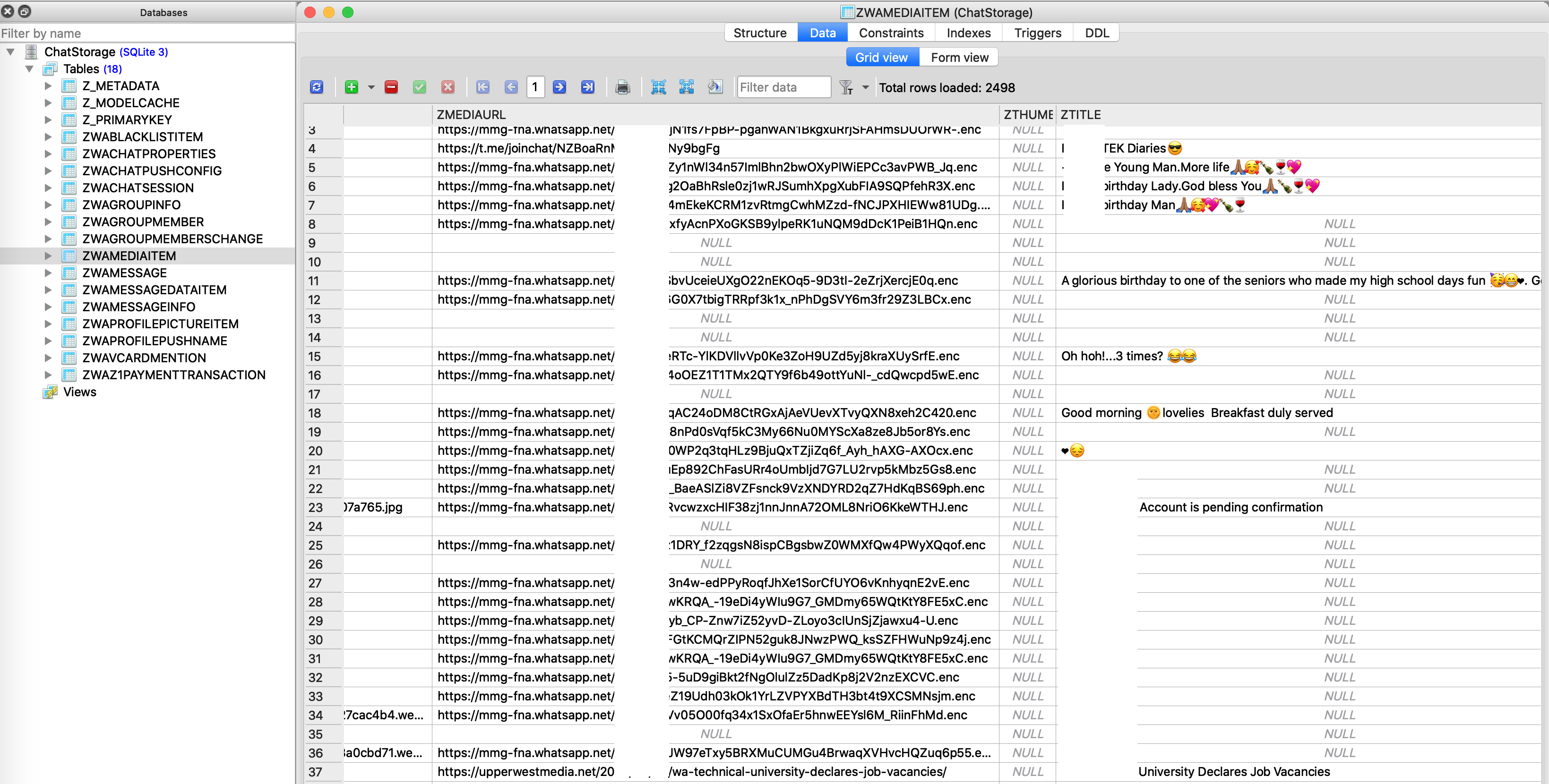
Fig. 9: Links to Encrypted Shared or Received Images/Documents
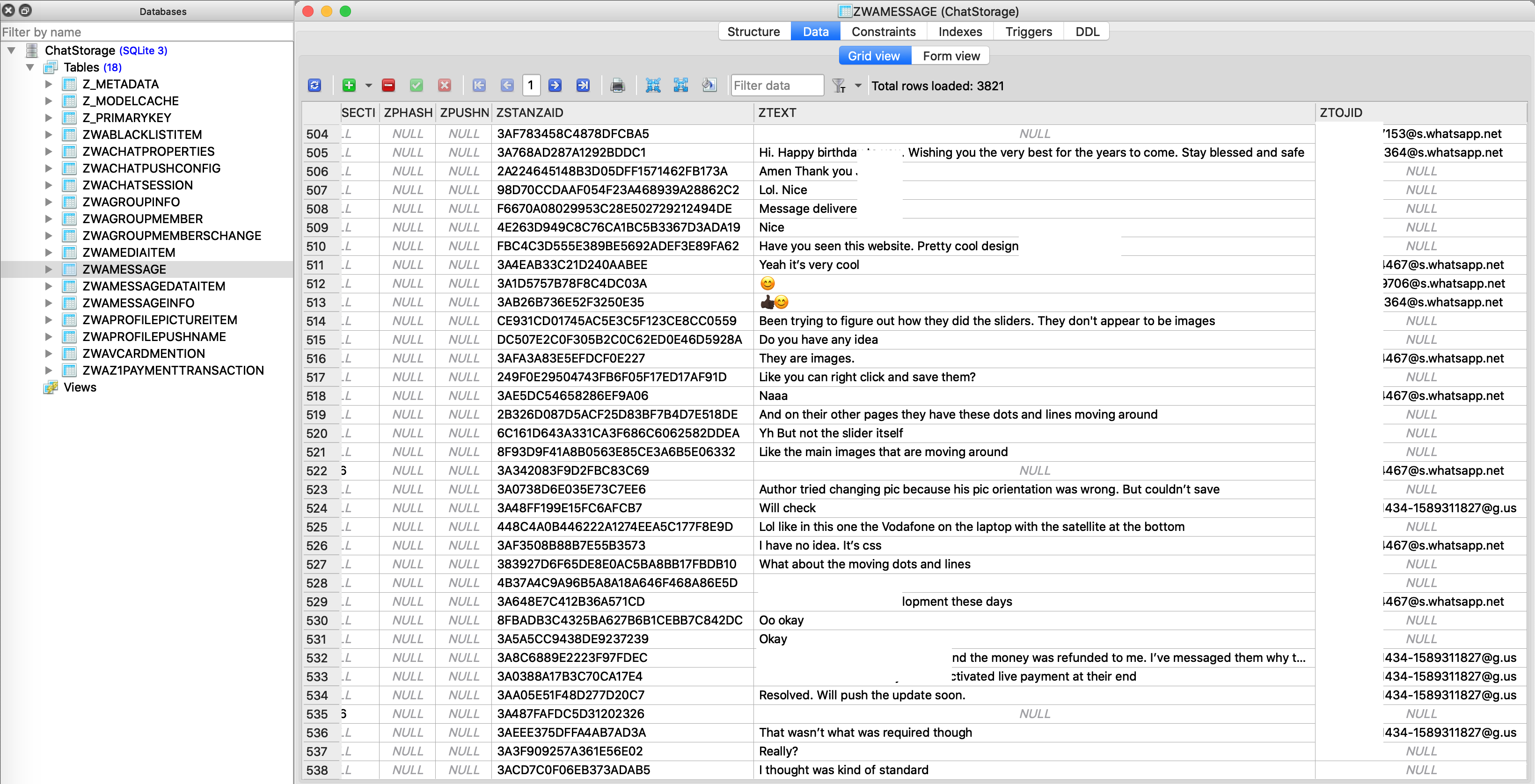
Fig. 10: Chat Messages
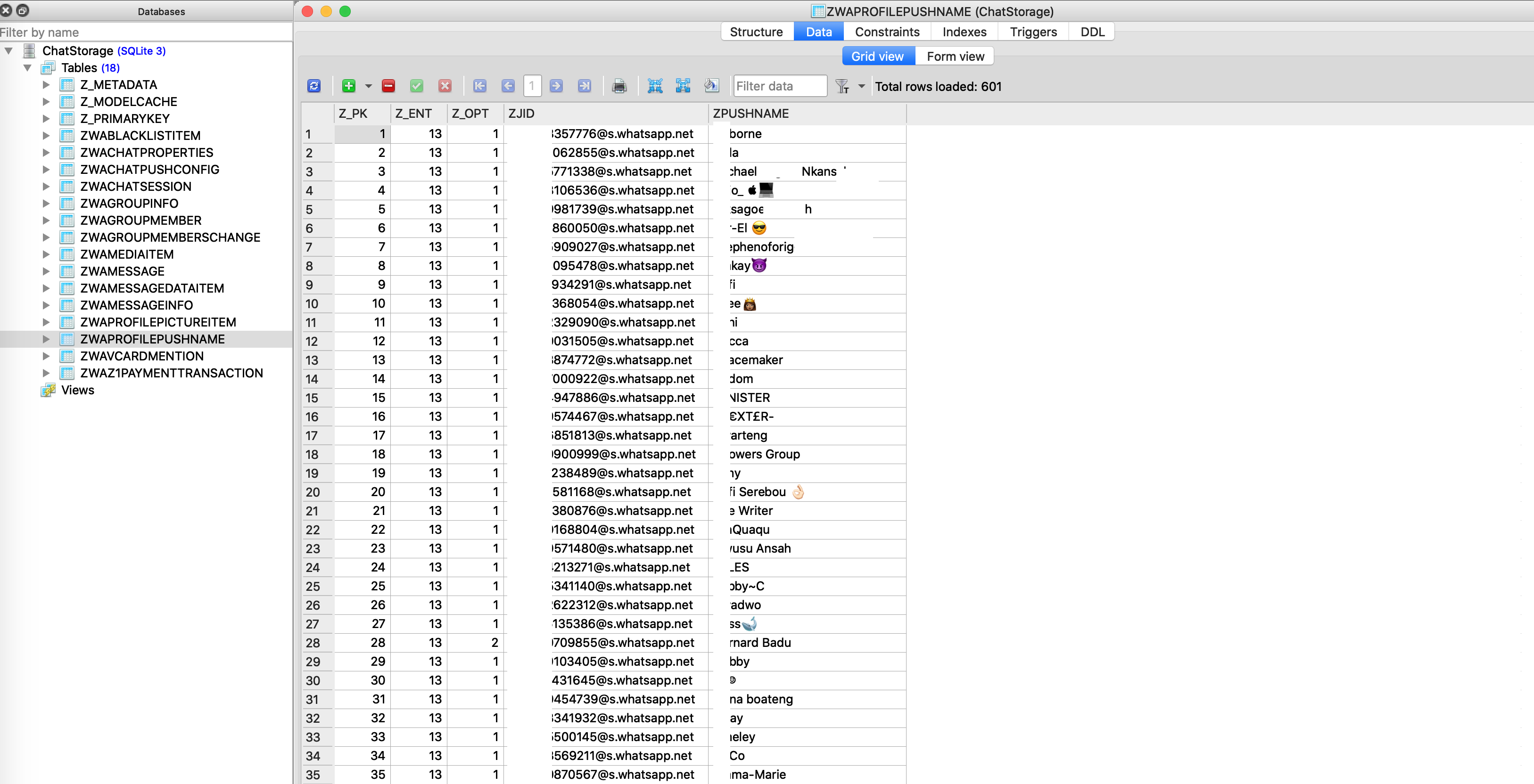
Fig. 11: Push Names of WhatsApp Contacts
Audio files (sent/received) are stored in .opus extension (shown in Fig. 12).
Fig. 12: Audio Files(s)
WhatsApp has a privacy consent that enables them to upload all contacts on a user’s phone to their server. This is shown in Fig. 13.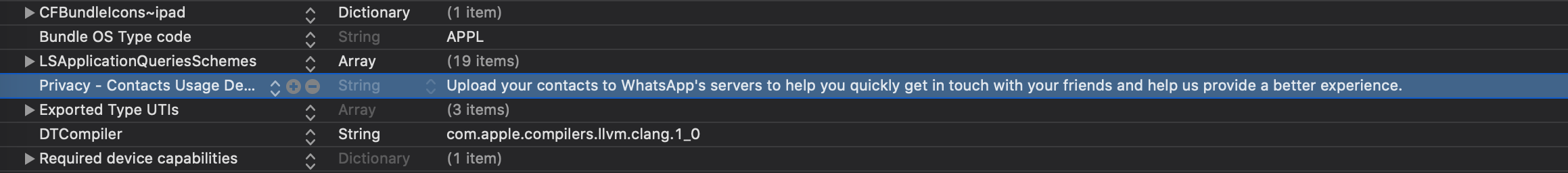
Fig. 13: Privacy Consent to upload contacts to WhatsApp’s Server
A copy of all contacts on a user’s phone is stored in “ContactsV2.sqlite”. This is shown in Fig. 14 and 15.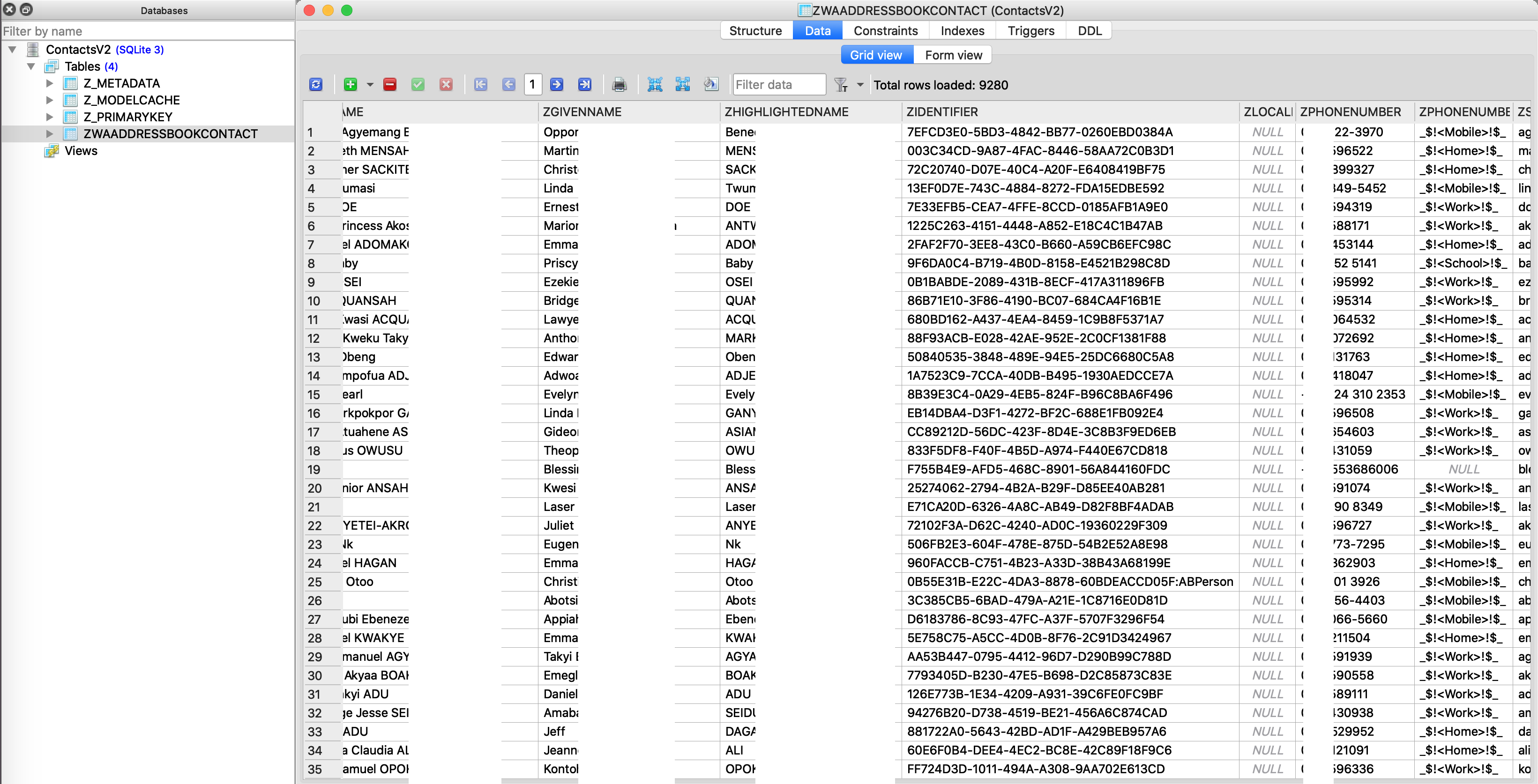
Fig. 14: User’s contacts collected and uploaded to WhatsApp’s Server
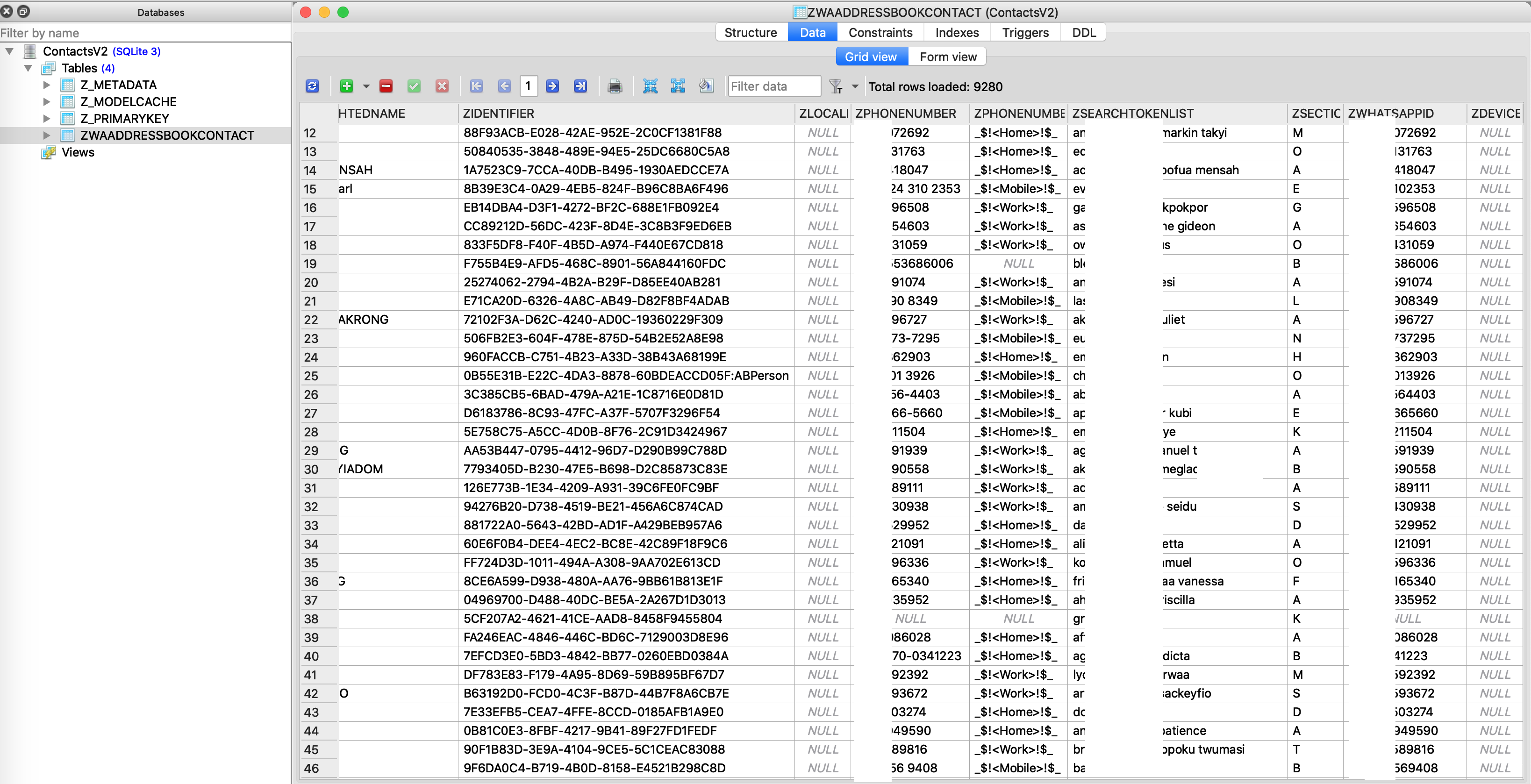
Fig. 15: User’s contacts collected and uploaded to WhatsApp’s Server
From the above security analysis, it can be observed that most of the data stored on the device is in plain text. Hence, it can be inferred that WhatsApp does not implement a secured on-device data storage mechanism.
Conclusion and Recommendation
This research analyzes how WhatsApp secures on-device data of its users. It has been demonstrated how WhatsApp’s data is not securely stored on end-users' devices; hence can be retrieved by an attacker who has physical access to the device.
It is recommended that WhatsApp implements a secure data storage mechanism for its users to protect them against instances where the physical device is compromised.
Reference List
-
unc0ver, https://unc0ver.dev.
-
How to Jailbreak iOS 13.5 on iPhone or iPad using Unc0ver Jailbreak, [Accessed Online] https://www.iphonehacks.com/2020/05/how-jailbreak-ios-13-iphone.html.
-
Unauthorized modification of iOS, https://support.apple.com/en-us/HT201954, 2020.

